Penetration testing, often shortened to "pen testing," has become an essential part of cybersecurity strategies for modern enterprises and government organisations in Australia and abroad. But what exactly is it—and does your organisation really need it?
This article will demystify penetration testing, explain its goals, when you need one, and how it compares to other assessments like vulnerability scans. If you're responsible for security, compliance, or digital transformation, this guide is for you.
Penetration Testing Explained
A penetration test is a simulated cyberattack designed to identify vulnerabilities in your systems, networks, or applications. These tests are carried out by ethical hackers who use real-world tactics to find security gaps before malicious actors do.
Unlike automated tools, penetration testers take a contextual approach—thinking like an attacker to uncover not just what vulnerabilities exist, but how they can be chained together to cause real damage.
According to the Open Worldwide Application Security Project (OWASP), pen testing is a critical step in securing applications, especially when aligned with frameworks like the OWASP Top 10.
The 6 Stages of a Penetration Test
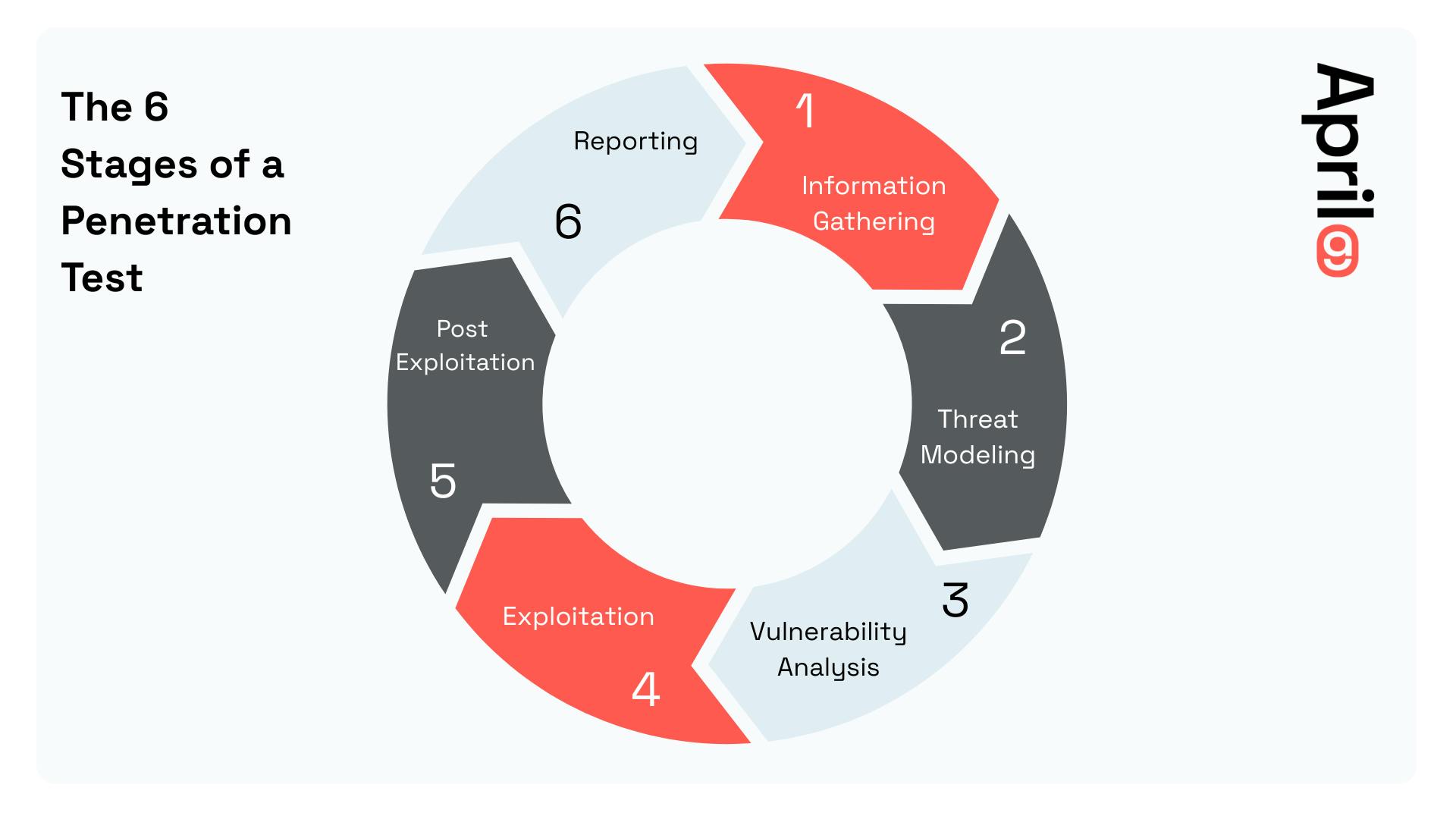
A professional penetration test isn’t just a single action — it’s a structured process that simulates how an attacker would work through your environment to uncover and exploit weaknesses. Most tests follow a version of the six-stage model shown below:
1. Information Gathering
This phase involves passive and active reconnaissance to identify public information, open ports, known software, or leaked credentials that could be used in an attack.
2. Threat Modeling
We analyse which assets are most attractive to attackers and map out potential entry points or paths based on your environment and risk profile.
3. Vulnerability Analysis
Automated and manual techniques are used to identify misconfigurations, exposed services, outdated software, and exploitable flaws in applications or infrastructure.
4. Exploitation
Here, ethical hackers attempt to exploit vulnerabilities to gain unauthorised access — proving real-world risk rather than just theoretical flaws.
5. Post-Exploitation
We explore how far an attacker could go: lateral movement, data access, privilege escalation, or persistence within your environment.
6. Reporting
The findings are compiled into a comprehensive report with severity ratings, technical details, and remediation guidance — along with an executive summary for non-technical stakeholders.
Key Goals of a Pen Test
- Identify vulnerabilities in apps, systems, networks, and configurations
- Test the effectiveness of existing security controls
- Simulate real-world attack paths to understand business impact
- Support compliance with frameworks like ISO 27001 or IRAP
- Provide actionable guidance for remediation and risk reduction
At April9, we tailor our pen tests to align with business priorities—whether you're concerned about data breaches, ransomware, or regulatory exposure.
Common Scenarios That Trigger Pen Testing
Penetration testing is often scheduled around:
- Major system or infrastructure changes
- Compliance audits (e.g. ISO 27001, IRAP)
- Security incidents or near-misses
- New app launches or migrations to the cloud
- Board or executive-level requests for assurance
Australia's ACSC recommends proactive testing as part of a risk-based security posture, especially for critical infrastructure or public-facing services.
Who Should Perform It? (Internal vs Third-Party)
While some larger organisations have internal red teams, most businesses benefit from third-party penetration testing for its independence, objectivity, and wider tooling knowledge.
Third-party benefits include:
- Broader exposure to emerging threats
- Unbiased risk analysis
- Often required for compliance or insurance
April9's testers hold industry certifications and follow best practices aligned with OWASP, PTES, and MITRE ATT&CK.
When You Definitely Need One
You likely need a penetration test if:
- You're storing or transmitting sensitive or regulated data
- You're preparing for ISO 27001, IRAP, or PCI-DSS audits
- Your systems have not been tested in the past 12 months
- You’ve recently deployed new applications or infrastructure
- You want a clear picture of your cyber risk posture
In many cases, your insurance provider or board may also request one.
How It Differs from Other Assessments
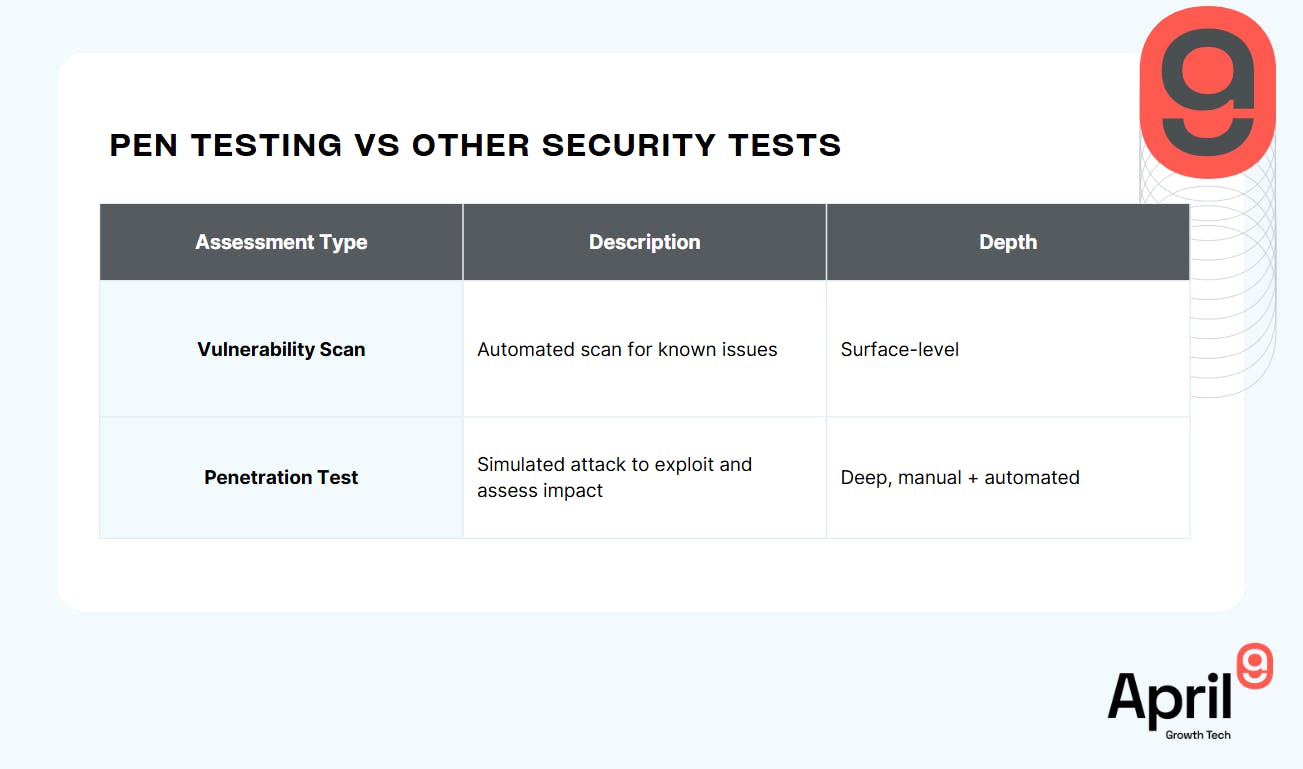
A common misconception is that penetration testing is the same as vulnerability scanning. It’s not.
A vulnerability scan might tell you what’s broken. A pen test tells you how bad it could be if exploited.
What Happens After the Test?
Once testing is complete, you’ll receive a detailed report with:
- A prioritised list of vulnerabilities (with severity ratings)
- Proof-of-concept evidence for critical findings
- Clear remediation steps
- An executive summary for non-technical stakeholders
Some providers stop there—but April9 goes further. We offer remediation support, retesting, and integration with your long-term security strategy.
Ready to Find Out Where You Stand?
Penetration testing isn’t just a compliance checkbox—it’s one of the most effective ways to protect your systems and build trust with customers, regulators, and stakeholders.
Learn more about April9’s Penetration Testing Services
Whether you’re preparing for an audit or simply want peace of mind, we can help.









